CMMC 2.0: Giving Defense Contractors More Time to Do Less (on Cybersecurity)
CMMC 2.0 simplifies the certification regime to:
- focus on industry-standard safeguarding requirements published by the National Institute of Standards and Technology (i.e. NIST SP 800-171, NIST SP 800-172),
- allow for self-certification rather than third-party assessment in many instances (which is a two-edged sword, as described below),
- permit compliance flexibility through use of Plans of Action and Milestones (POAMs) and waivers, and
- suspend piloting efforts and postpone mandatory compliance until completion of rulemaking on both 32 CFR and 48 CFR.
Although these changes appear to lessen the burden on contractors (granting more time while reducing requirements), defense contractors are nonetheless well advised to proactively manage cybersecurity threats.
US information networks are targets of cyberattacks every day, and cyber threats continue to evolve. The Defense Industrial Base (DIB) is a prominent target for cyberattacks, which are becoming ever more frequent and complex.
As part of its efforts to implement Section 1648 of the NDAA for fiscal year 2020 and better protect against cyber threats, the DoD developed the CMMC program to safeguard sensitive controlled unclassified information (CUI) that is shared by the DoD with its contractors by incorporating a cybersecurity certification requirement into the defense contracting process. The initial CMMC framework was published in an Interim Rule which took effect November 20, 2020, and mandated that by 2025, most defense contracts would require prime and subcontractors to be certified by an accredited third-party assessor organization as meeting one of five levels of cybersecurity maturity.
In March 2021, Deputy Secretary of Defense Kathleen Hicks directed an internal DoD review of the CMMC program to determine whether the program was accomplishing its stated goals without creating unnecessary barriers for defense contractors. As part of the review, the Department conducted more than 1,000 interviews about challenges and questions surrounding the CMMC program and considered the more than 850 public comments that were submitted. The review produced significant changes to the program. Those program changes were announced on November 4, 2021 as CMMC 2.0.
To Whom Do CMMC 2.0 Requirements Apply?
The CMMC 2.0 requirements, like most procurement regulations, apply to contractors and subcontractors only to the extent the CMMC contract clause appears in their agreements. As of the effective date of the Interim Rule, the previous CMMC clause is no longer approved for inclusion in DoD contracts, and a new clause to implement the framework of set forth in the Interim Rule remains forthcoming. It is expected the new clause will be required in all DoD contracts and subcontracts other than those for commercial-off-the-shelf (COTS) items. Where the clause appears in a contract, it is expected to impose requirements on contractors and subcontractors that obtain and/or handle Federal Contract Information (FCI) and CUI.
Under CMMC 2.0, not all contractors will be required to obtain third-party assessments of their cybersecurity maturity. Instead, contractors undergo either a self-assessment, third-party assessment, or government assessment, based on the hierarchical CMMC level sought. For CMMC Level 1, applicable to defense contractors that do not process, store, or transmit CUI, but do process, store or handle FCI, only a self-assessment is required, the results of which are to be submitted to DoD accompanied by the affirmation of a senior company official. For CMMC Level 2, some contractors will be permitted to submit self-assessments if they do not handle information deemed critical to national security. The remaining Level 2 contractors will be required to undergo a cybersecurity maturity assessment by a Certified Third-Party Assessment Organization (C3PAO). For CMMC Level 3, contractors will have to undergo a government-led assessment of their cybersecurity maturity and compliance.
The ability to self-certify is a double-edged sword that should be used with caution. Without a doubt, self-certification might be lower cost and accomplished on a more congenial schedule than a third-party certification. Those benefits must be weighed, however, against the benefit of the rigor of neutral third-party review, and the legal benefit of not having to make an express certification that might later prove inaccurate.
What Are the Requirements of the CMMC 2.0 Program, What’s Different From Version 1.0, and What Do the Changes Mean for Defense Contractors?
CMMC 2.0 collapses the original cybersecurity maturity model framework from five levels to three (old “transitional” levels 2 and 4 have been dropped), which will simplify the program for both contractors and the DoD. Of greater effect, CMMC 2.0 removes all CMMC-unique practices and all maturity processes from all levels and allows for self-assessments in many instances, as noted above and shown in the chart below.
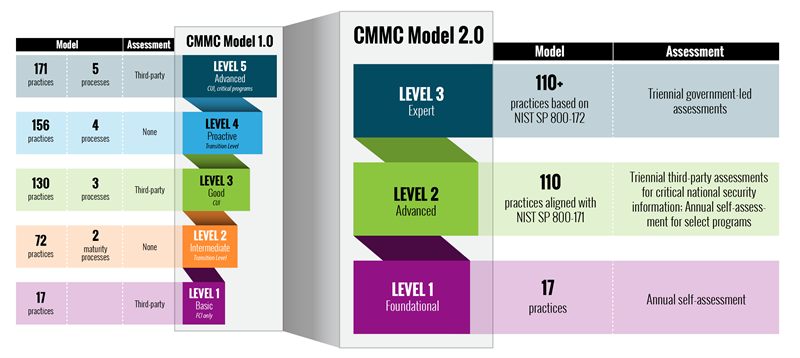
 At this juncture, it appears Level 1 compliance under Version 2.0 will remain the same as under Version 1.0, requiring the implementation of 17 basic security practices, which have long been required under FAR 52.204-21, “Basic Safeguarding of Contractor Information Systems,” and consist of a subset of the requirements set forth in the NIST SP 800-171 (although theoretically possible, it seems unlikely changes would be made to the 17 basic security practices that were required under CMMC 1.0).
At this juncture, it appears Level 1 compliance under Version 2.0 will remain the same as under Version 1.0, requiring the implementation of 17 basic security practices, which have long been required under FAR 52.204-21, “Basic Safeguarding of Contractor Information Systems,” and consist of a subset of the requirements set forth in the NIST SP 800-171 (although theoretically possible, it seems unlikely changes would be made to the 17 basic security practices that were required under CMMC 1.0).
Under CMMC 2.0, Level 2 compliance will require satisfactory implementation of all 110 requirements set forth in NIST SP 800-171 (with the exceptions noted below for POA&Ms and waivers). Most existing defense contractors already are familiar with NIST SP 800-171, compliance with which has been required under DFARS 252.204-7012, “Safeguarding covered defense information and cyber incident reporting” since late 2017, such that the only new or additional requirement associated with CMMC 2.0 Levels 1 and 2 will be the requirement for an attestation of a senior company official that must accompany self-assessments.
The model for Level 3, which is still under development, will include the requirements of NIST SP 800-171, plus a subset of the NIST SP 800-172 enhanced security requirements. The additional protective measures outlined in NIST 800-172 were developed for use by agencies when sharing CUI associated with a critical program or a high-value asset which is a potential target for advanced persistent threats. These requirements form the foundation for a “multidimensional, defense-in-depth protection strategy that includes three mutually supportive and reinforcing components: (1) penetration-resistant architecture, (2) damage-limiting operations, and (3) designing for cyber resiliency and survivability.” Designed to supplement the basic and derived security requirements in 800-171, subsets of the 800-172 requirements can be selected to fit the specific mission and business purposes of the agency or program.
In addition to streamlining the certification program, CMMC 2.0 adds flexibility in two respects: in certain circumstances, companies will not be prohibited from seeking contracts despite not meeting CMMC requirements if they can present POAMs that evidence a concrete plan and steps to be taken toward certification; and in limited circumstances, companies may be granted certification waivers for select mission-critical requirements, with senior DoD leadership approval and for a limited duration.
What Is the Time Frame for Implementation?
The phased rollout of CMMC 1.0 has been canceled. This is unsurprising since the phased rollout provided that 15 contracts would include CMMC requirements in FY 2021, but no such contracts were announced before the end of the fiscal year.
CMMC 2.0 will not go into effect until after the rulemaking on 32 CFR to define the CMMC regime more fully, and after the rulemaking on 48 CFR to update the procurement code. The agency estimates the rulemaking may take 9 to 24 months. That timeframe, which seems optimistic, means that across-the-board implementation could come as early as the fourth quarter of 2022. Although that date is three years earlier than the now-abandoned phased rollout of CMMC 1.0, CMMC 2.0 allows both for POAMs and waivers – removing the hard-edge compliance deadline.
Questions Remain
Although the DoD and third-party assessment organizations are urging companies to get their cyber houses in order early – indeed the DoD is “exploring opportunities to provide incentives for contractors who voluntarily obtain a CMMC certification in the interim period” – uncertainty abounds because details of CMMC 2.0 are yet to be announced.
Questions contractors are asking include:
- Which compliance levels must I meet, and what are the exact requirements?
The required compliance level will be specified in DoD solicitations and RFIs. The Department of Defense intends to post the Level 1 and 2 models, their associated Assessment Guides, and scoping guidance in the coming weeks, with Level 3 model information – which is still under development – posted “as it becomes available.” In the interim, DOD invites contractors to look at DoD’s Project Spectrum, which was developed to help companies evaluate and improve their cybersecurity maturity.
- Will the Government provide financial assistance for small businesses that would be forced out of the defense industrial base if required to foot the entire assessment process bill?
No financial assistance is directed to small business compliance. On cost reimbursement contracts, compliance costs should be allowable costs for both small and non-small businesses alike. And of course, the Government’s view is that CMMC 2.0 enhances the certification regime “by . . . reducing costs, particularly for small businesses” by allowing self-assessments, allowing contractors to proceed with POAMs, and allowing waivers.
- Will there be enough C3PAOs to conduct timely assessments for the tens of thousands of companies that may ultimately need them since the CMMC Accreditation Body’s website lists only 5 accredited C3PAOs so far?
Time will tell. There are a number of process hurdles and resource limitations slowing the certification of C3APOs, which gives contractors who will likely need third-party assessments more time to get ready. Those that may be ready should watch the CMMC 2.0 website for more information about incentives for early volunteer certification, as those could impact the timing of their assessment decisions.
- How will CMMC 2.0 affect non-US companies?
The now-retired CMMC clause in the DFARS was applied to prime contractors and flowed down to subcontractors without respect to the jurisdiction in which the contractor or subcontractor was organized. Interestingly the DoD has raised the possibility of applying CMMC only to U.S. companies. The DoD states that it “intends to engage with our international partners to establish agreements” to address application of cybersecurity maturity certification requirements to foreign contractors, and these agreements will be addressed in the rulemaking process. The DoD does not explain why it would consider granting an exception for non-U.S. companies in an area where all companies previously were treated alike.
- What impact will the anticipated GAO report have on the program?
GAO is conducting its own audit of the CMMC program. The GAO’s draft report is currently with the DoD for review and comment, and the GAO has not yet announced an official publication date for the final report. Preliminary findings announced earlier this year by one of the participating industry groups included several proposed reforms. Whether those recommendations will be included in the GAO report is unclear.
- Can the attestation required for self-certification be the basis for a False Claims Act (FCA) prosecution?
The potential use of a CMMC 2.0 self-certification in the context of allegations of violations of the False Claims Act is, in part, what makes self-certification a two-edged sword. The materiality of a CMMC 2.0 compliance will be an open question in any FCA case and should not be presumed. Where such compliance is material, there are clear substantive and procedural benefits to relying on a third-party certification. In view of DOJ’s establishment of its Civil Cyber-Fraud Initiative, escaping a third-party assessment requirement could be a mixed blessing, and companies should take the self-assessment process very seriously.
Arent Fox attorneys will continue to monitor developments. If you are interested in discussing steps your company should consider toward CMMC 2.0 certification, please contact Cissy Jackson, Travis Mulley, Kevin Pinkney, or another member of Arent Fox’s Government Contracts Group, or the Arent Fox attorney which whom you already work.
Contacts
- Related Practices


